Log Miner App for Monitoring Splunk Event PatternsPowered by Big Data Science Research
Introduction to Splunk Events and Environment Health
-
- Splunk is a Log Analytics platform
- Captures real time log events data from applications or systems software.
- Enables answering any kind of questions based on such log data
- Splunk generates log events based on user or system actions on the platform
- Splunk environment can face many issues in areas such as:
- Search performance, Installation or upgrade, Indexing, Cluster setup, Reporting etc.
- Splunk is a Log Analytics platform
Log Miner App for Splunk Environment – How it Helps?
This App is developed to be useful for Splunk administrators who are managing Splunk environments.
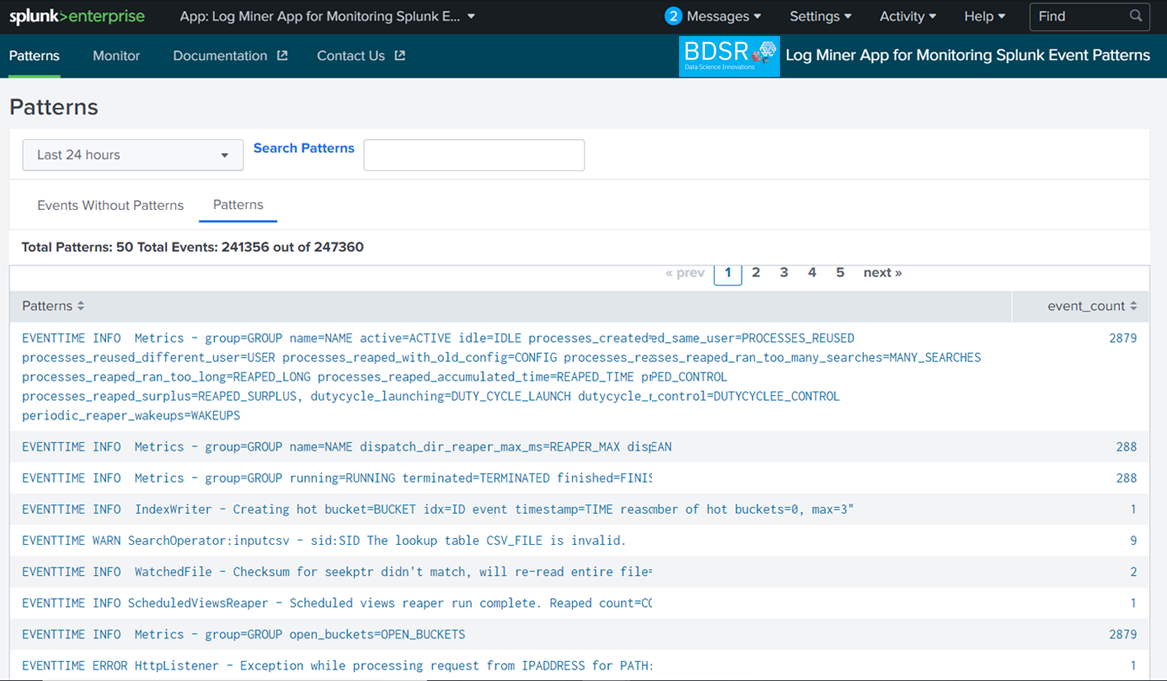
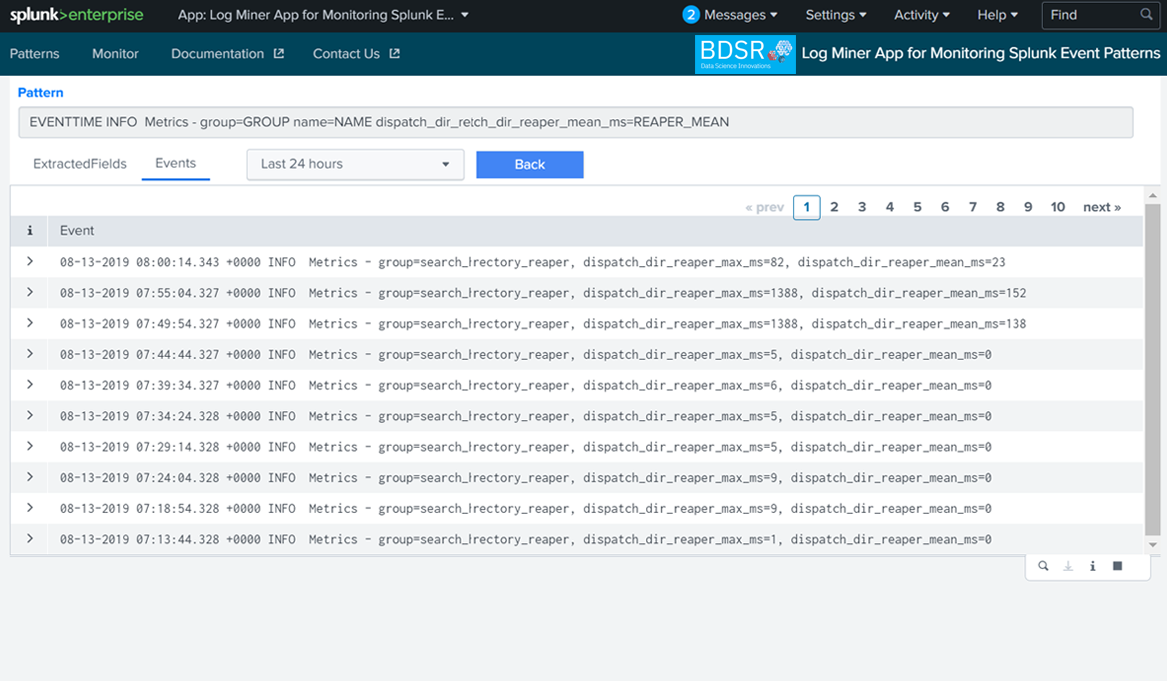
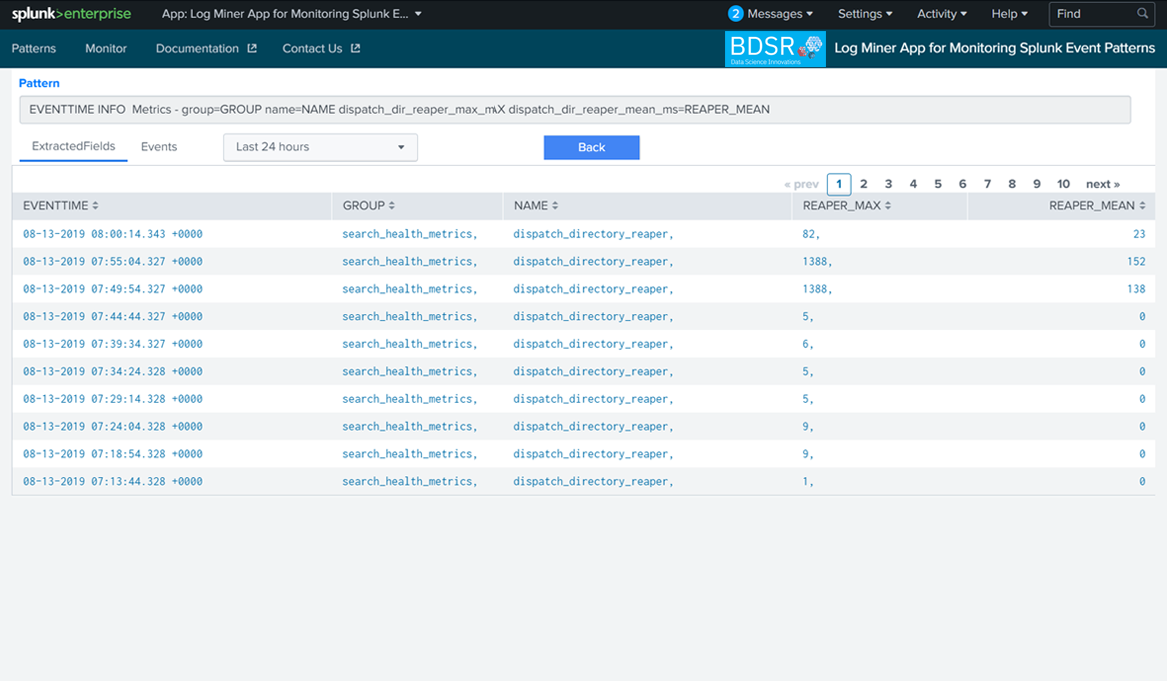
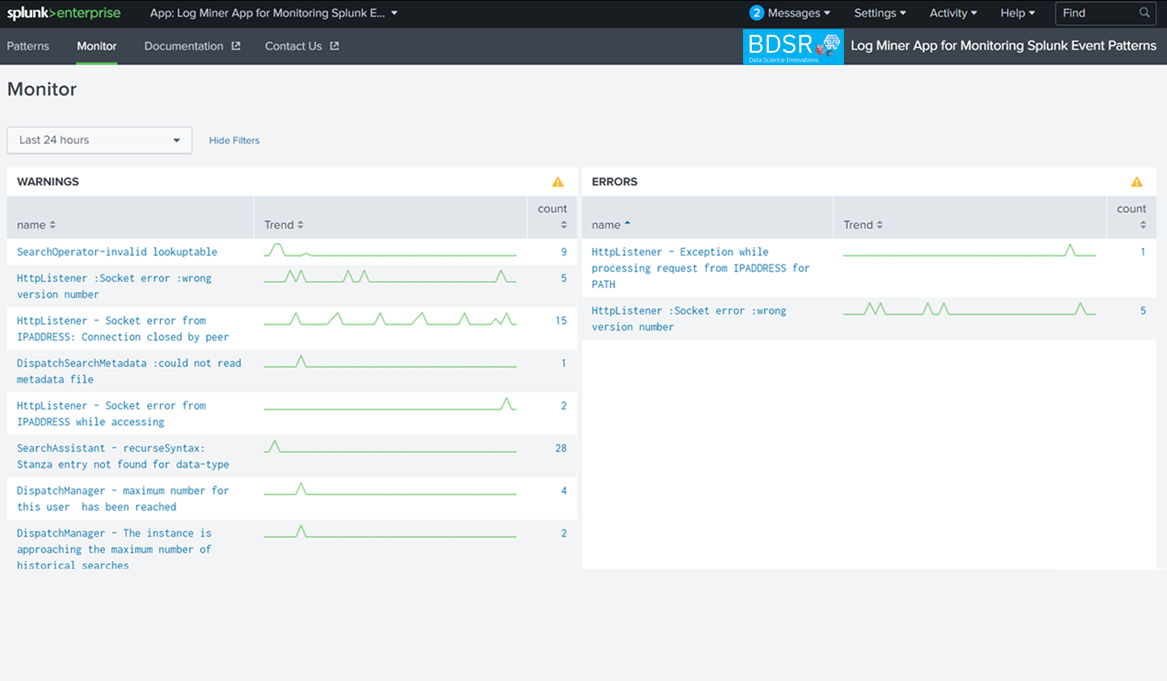
It provides following quick insights
It provides following quick insights
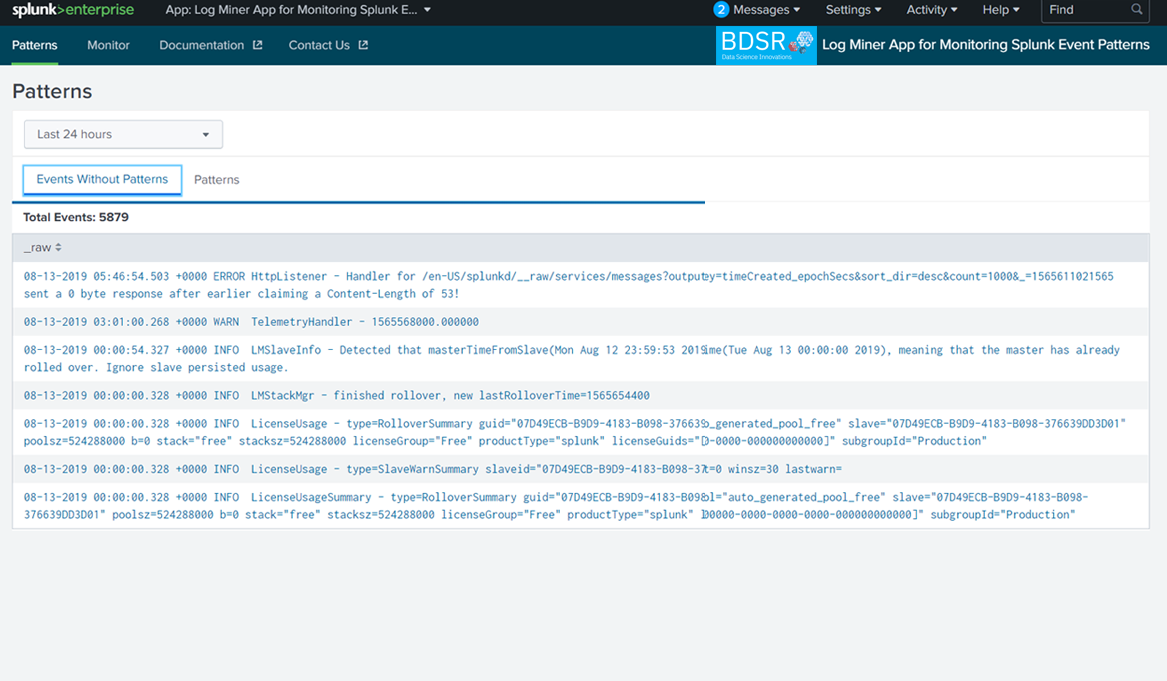
Show the events for which patterns are not available in the App event patterns DB With the above insights, Administrators can quickly identify issues happening in their Splunk environments and resolve the issues.
We have mined patterns for the events generated by our development Splunk environment. These patterns may cover only a subset of all possible patterns that Splunk generates in production environments. Interested users, please reach out to us using “Contact Us” page in the app for discovery of patterns relevant to your environment.